Configure HTTPS/TLS on the Kloudfuse Ingress
You can configure the Kloudfuse stack to work on clusters that have HTTP/TLS using Ingress rules. You can use the cert-manager and lets-encrypt to create certificates, or use an existing certificate.
Complete these tasks to fully configure HTTP/TLS with Ingress rules.
Prerequisites
-
A DNS host name.
-
A static external IP address associated with the DNS host name, for the ingress load balancer.
-
GKE
-
AWS
Reserve a static external IP.
See Google documentation on how to Configure static external IP addresses.
Allocate IP addresses from AWS Elastic IP.
See AWS documentation on Elastic IP addresses.
-
-
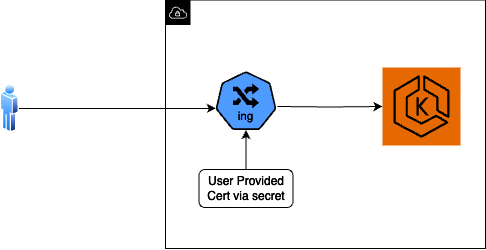
A certificate, either a new SSL certificate created as part of Kloudfuse installation, or an existing SSL certificate.
-
New Certificate
-
Existing Certificate
If the SSL certificate is created as part of Kloudfuse installation, then cert-manager using lets-encrypt creates the Certificate. Ihe cert-manager must be installed already in the Kubernetes cluster. See cert-manager documentation on Installation.
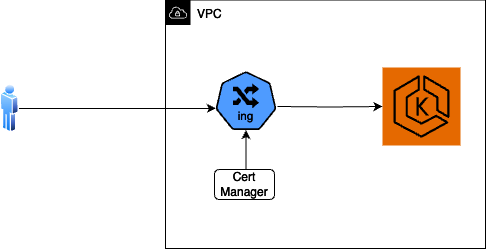 Create certificate during install
Create certificate during installhelm repo add jetstack https://charts.jetstack.io helm repo update helm install cert-manager jetstack/cert-manager --create-namespace --namespace kfuse --version v1.7.1 --set installCRDs=trueyml -
Configure Helm Values
Depending on the cloud provider and certificate method, add the following entries in the custom_values.yaml file:
-
GCP or Azure, New Certificate
-
GCP or Azure, Existing Certificate
tls:
enabled: true
host: <REPLACE DNS HOST HERE>
email: <REPLACE EMAIL>
clusterIssuer: <PROVIDE A CLUSTER ISSUER NAME. ensure that this is unique within the cluster>
ingress-nginx:
controller:
ingressClassResource:
enabled: true
name: kfuse-ingress
ingressClass: kfuse-ingress
watchIngressWithoutClass: false
service:
loadBalancerIP: <REPLACE PRE-ALLOCATED STATIC IP HERE>
external:
enabled: truetls:
enabled: true
host: <REPLACE DNS HOST HERE>
email: <REPLACE EMAIL>
clusterIssuer: <LEAVE BLANK because providing own ssl certificate>
secretName: <PROVIDE secret name containing SSL certificate, such as kfuse-tls> (1)
ingress-nginx:
controller:
ingressClassResource:
enabled: true
name: kfuse-ingress
ingressClass: kfuse-ingress
watchIngressWithoutClass: false
service:
loadBalancerIP: <REPLACE PRE-ALLOCATED STATIC IP HERE>
external:
enabled: true| 1 | secretName created in Use an existing certificate. |
Disable HTTP traffic
|
If you plan to disable HTTP traffic completely, add the following to the ingress-nginx section in custom-values.yaml file:
ingress-nginx:
controller:
service:
enableHttp: falseauto installed certificates